Earlier this year, on January 23rd, the NCSC and the IASME Consortium, announced that new technical requirements for the government backed Cyber Essentials scheme would be coming into place on 24th April 2023.
This update is part of the routine revaluation of the Cyber Essentials scheme’s technical controls so that the certification can continue to protect UK organisations against common cyber threats.
As with the last update we previously explained What’s New in 2022, and here’s what you need to see in 2023.
What’s changing?
Firmware now included as a type of software in scope
With italics showing the added text the definition of ‘software’ has been updated in the requirements to the following: “Software includes operating systems, commercial off-the-shelf applications, plugins, interpreters, scripts, libraries, network software and firewall and router firmware.”
Why? – According to IASME as firmware is the operating system for the “key security devices” firewalls and routers, “whether they are kept up to date is extremely important from a security perspective.”
Further to this, although Cyber Essentials requires that an applicant’s laptops, desktops, servers, computers, tablets and mobile phones be listed including their make and operating system, for firewalls and routers only the make and model need to be detailed. From this information an Assessor can establish if security updates are being received by the firmware.
Emphasis on asset management
Asset management should be considered “as a core security function” because effective use of it can assist in satisfying all five controls.
Why? – With asset management impacting multiple business functions, including IT operations, financial accounting, managing software licences, procurement and logistics - with inevitable overlaps and dependencies between each - its proper integration and coordination within an organisation is essential to reduce or manage conflicts.
The requirements state that “Effective asset management doesn’t mean making lists or databases that are never used. It means creating, establishing and maintaining authoritative and accurate information about your assets that enables both day-to-day operations and efficient decision making when you need it.”
IASME explain that “many major security incidents are caused by organisations having assets which are still connected to the network when that organisation is not aware the asset is still active. Effective asset management will help track and control devices as they’re introduced into your business.”
A link is also included to this more comprehensive guidance from the NCSC on asset management.
Bring your own device information added
Further advice has been given in order to clear up ambiguity stemming from the bring your own devices (BYOD) trend.
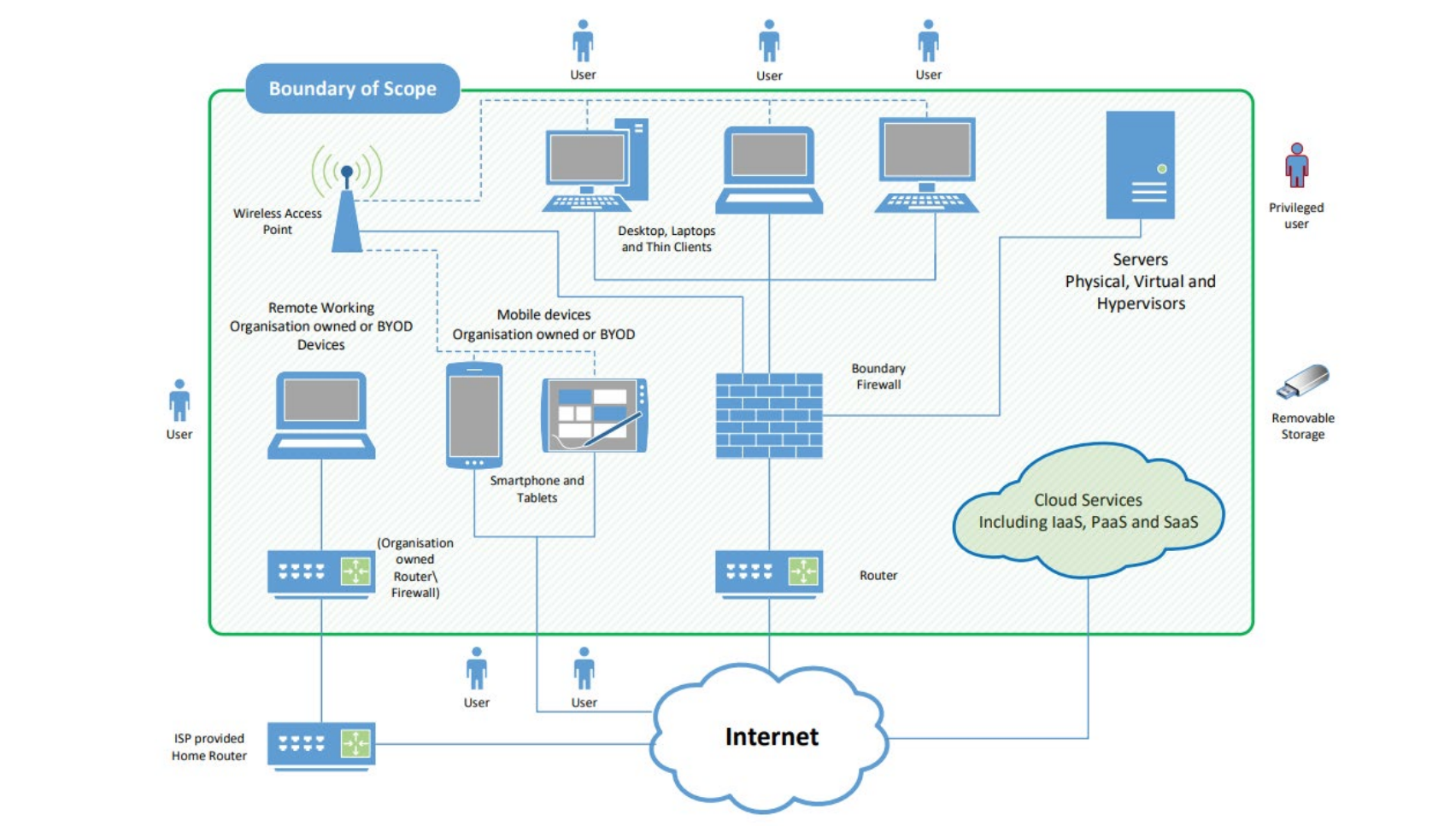
Why? - With customised experiences “making consistent implementation of the controls more challenging” the new technical requirements designate user-owned devices which access organisational data or services (as illustrated in the below image) as in scope.
All mobile or remote devices used only for the purpose of native voice applications, native text applications, or multi-factor authentication (MFA) applications are out of scope.
Further NCSC guidance on the use of BYOD can be found here.
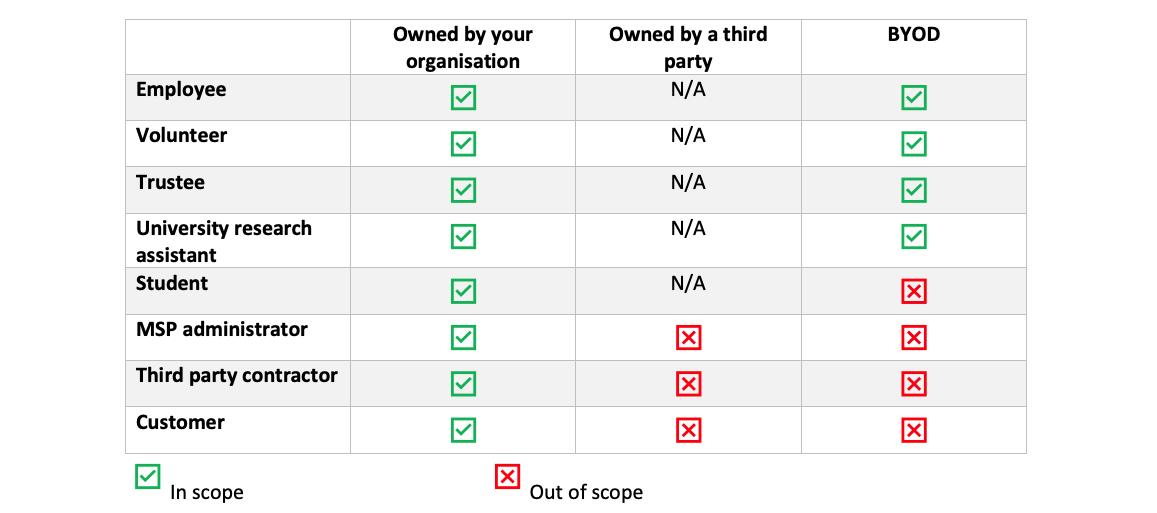
Scope of third party devices clarified
“All end user devices your organisation owns that are loaned to a third party must be included in the assessment scope,” explains the new requirements.
The below table further simplifies whether other devices - such as those not owned by your organisation – are in or out of scope.
Why? – Due to the frequent questions on third party devices for students, volunteers, consultants etc this guidance demonstrates that an organisation must be able to apply the required controls via a combination of technical and written policy.
With IASME stating that “the devices of students that are not owned by the applicant organisation are not and have never been in scope.”
Updated ‘Device Unlocking’ guidance
Due to concerns that some vendor’s own default settings can’t be altered, Cyber Essentials advises that the applicant use the minimum allowed by a vendor’s default setting.
Why? – IASME explains that sometimes “an applicant might be using a device where there are no options to change the configuration to meet the Cyber Essentials requirements. One example of this is locking the device after 10 failed sign-in attempts. Samsung, possibly the largest provider of smartphones in the world, have set their minimum sign-in attempts at 15, with no option to alter this number.”
The new requirements state that “When the vendor doesn't allow you to configure the above, use the vendor’s default setting.”
All devices in scope must have active malware protection
For each device, you must use at least one of the options listed below.
In most modern products these options are built in to the software supplied. Alternatively, you can purchase products from a third-party provider. In all cases the software must be active, kept up to date in accordance with the vendors instructions, and configured to work as detailed below:
Anti-malware software (option for in scope devices running Windows or MacOS including servers, desktop computers, laptop computers) If you use anti-malware software to protect your device it must be configured to:
- be updated in line with vendor recommendations
- prevent malware from running
- prevent the execution of malicious code
- prevent connections to malicious websites over the internet.
Application allow listing (option for all in scope devices) Only approved applications, restricted by code signing, are allowed to execute on devices. You must:
- actively approve such applications before deploying them to devices
- maintain a current list of approved applications, users must not be able to install any application that is unsigned or has an invalid signature.
Why? - In this case guidance has been updated to reflect the latest knowledge, research and recommendations from vendors.
Cyber Essentials doesn’t prevent you using a zero trust architecture
Developments such as the increased number of services moving to the cloud, the growing use of Software as a Solution (SaaS) and organisations embracing flexible working have led to changes in network architecture.
As many different device types, from multiple locations, connect to a system a zero trust architecture is used to protect the network. It is an approach to system design where “the network is assumed hostile and each access is verified, based on an access policy,” according to the NCSC.
“Confidence in a request is achieved by building context, which relies on strong authentication, authorisation, device health, and value of the data being accessed.”
The new technical requirements state that “As organisations move towards zero trust architecture models, we have considered it in this context, and are confident that implementing the technical controls doesn't prevent you using a zero trust architecture as defined by the NCSC guidance.”
https://www.ncsc.gov.uk/collection/zero-trust-architecture
Further Updates
- This illustrative specification document for CE+ has been updated: https://www.ncsc.gov.uk/files/Cyber-Essentials-Plus-Illustrative-Technical-Specification-v3-1-January-2023.pdf
Changes regarding malware protection affect how a CE+ Assessor carries out the malware protection tests. In a CE+ audit, the Assessor will discuss further if required. - The technical requirements document has been updated with a number of style and language changes made to make the document more readable.
- The technical controls have been reordered to align with the self-assessment question set.
- For consistency, the scheme requirements are now in the same order as the question set which is, firewalls, secure configuration, security update management, user access controls, and malware protection.
For the full updated technical requirements for Cyber Essentials, see here.
How will this affect you?
This updated set of requirements is version 3.1 for the Cyber Essentials scheme. It will come into force on the 24th April 2023.
The ‘Montpellier’ question set will replace 'Evendine.' Additionally, the grace periods for some of the requirements from the 2022 update will end on 24th April.
It's important to note that any assessments that began before 24th April, will continue to use the requirements version 3.0 with the 'Evendine' question set. This includes any assessment accounts created before 24th April.
Further to this, any and all assessment periods remain the same. For Cyber Essentials Basic, you have 6 months to complete the assessment and pass from the moment you receive login details for the IASME portal. After gaining your Cyber Essentials certification you then have three months to complete the Cyber Essentials Plus assessment. This is a strict time limit, not a length of time to aim for.
In summary:
- The launch of the Montpellier Question Set (CEV3.1) is 24th April 2023.
- The last day to create Evendine Assessment accounts is 23rd April 2023.
- The last day to complete Evendine Assessments is 23rd October 2023.
- The last day to complete Evendine CE+ Assessments is 23rd January 2024.
- All Cyber Essentials accounts created from 24th April 2023 onward will be on Montpellier (CEV3.1).
The NCSC's Cyber Essentials FAQ’s
What happens if I gain Cyber Essentials certification using the current question set and requirements, but subsequently need to gain Cyber Essentials Plus after 24 April?
If you begin the Cyber Essentials process before 24 April, your Cyber Essentials Plus assessment will be carried out against the same question set and requirements. It must be completed within three months of the Cyber Essentials assessment.
Are there any circumstances in which the current requirements will still apply beyond the expiry date of 24 October 2023?
Yes. As your Cyber Essentials Plus assessment must be carried out within three months of beginning the Cyber Essentials process, if you begin the Cyber Essentials process before 24 April, it may mean that you complete the Cyber Essentials Plus assessment using the current requirements after the expiry date of 24 October 2023.
Who was involved in updating the technical standard?
The update was carried out by the NCSC and our Cyber Essentials delivery partner, the IASME Consortium. Many of the changes are based on feedback from assessors and applicants. Technical experts from the NCSC were also involved.
Is there a grace period allowed this year?
As this update doesn’t include any significant changes to the requirements and is lighter touch than the April 2022 release, there will be no grace period in place this time. Information about the current grace period is available on the NCSC website.
My organisation has other technical controls in place that don’t meet the new Cyber Essentials requirements. Can I use these to achieve certification?
Cyber Essentials is prescriptive and other controls are not currently permitted. However, we are currently considering how we may be able to help organisations in this situation. This project is still in the development phase and further information will be available in time.
For how long are the certificates valid?
All new certificates issued by IASME will have a 12-month expiry date.